
DOD Implements New Cybersecurity Requirements with Interim Rule
In Short
The Situation: The U.S. Department of Defense ("DOD") recently issued an interim rule to strengthen the defense contractor supply chain by rolling out the Cybersecurity Maturity Model Certification ("CMMC") framework and implementing a DOD Assessment Methodology to assess contractors' cybersecurity.
The Result: The interim rule, effective November 30, 2020, requires defense contractors to report assessments of their implementation of the National Institute of Standards and Technology Special Publication 800-171 ("NIST SP 800-171") controls to the DOD, and kicks off the phased implementation of the CMMC.
Looking Ahead: Companies doing business with the DOD should examine their level of compliance with the controls of NIST SP 800-171, complete and submit appropriate assessments, and consider how they plan to comply with the requirements of the CMMC to ensure that they are prepared to meet the cybersecurity requirements the DOD will be including in new contracts and when exercising options.
Rollout of CMMC Framework
On September 29, 2020, the DOD issued a much-anticipated interim rule initiating its phased five-year rollout of the CMMC. The interim rule defines each of the five cybersecurity levels for which contractors may obtain third-party certification, with each level building on the one before:
CMMC Levels and Descriptions:
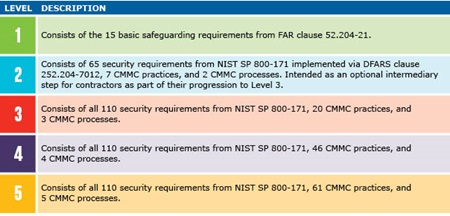
The interim rule explains that contractors must: (i) maintain the requisite CMMC level for the duration of the contract; (ii) ensure that its subcontractors also have the appropriate CMMC level prior to awarding a subcontract or other contractual instruments; and (iii) include the requirements of the CMMC clause in all subcontracts or other contractual instruments.
Beginning on November 30 of this year, the DOD will begin inserting DFARS 252.204-7021 in certain solicitations. Contracts that contain this provision will require compliance with the specified CMMC level. By October 1, 2025, the DOD will include the CMMC clause in all solicitations (including those for task and delivery orders and those for commercial items) above the micro-purchase threshold except solicitations that are exclusively for commercially available off-the-shelf ("COTS") items.
New Assessment Methodology
As the DOD phases in the CMMC, contractors subject to DFARS 252.204-7012 will need to obtain a cybersecurity "Assessment" under the newly announced "Assessment Methodology." This new methodology requires an assessment of the contractor’s implementation and compliance with NIST SP 800-171 at three different levels: Basic, Medium, and High. A Basic Assessment is based on a contractor’s self-representation of compliance. For both the Medium and High Assessments, the DOD will review the contractor’s system security plan description of how each NIST SP 800–171 requirement is met. Under a High Assessment, the DOD will require a contractor to demonstrate its system security plan.
The results of the assessments will be recorded in the Supplier Performance Risk System ("SPRS") and valid for three years. Beginning November 30, 2020, a contracting officer must, before awarding or renewing a contract containing DFARS 252.204-7012, check the SPRS database to confirm that the company has a current SPRS Assessment. The interim rule describes the Assessment Methodology and its framework in new DFARS clauses 252.204-7019, Notice of NIST SP 800-171 DOD Assessment Requirements and 252.204-7020, and NIST SP 800-171 DOD Assessment Requirements.
Three Key Takeaways
- Companies doing business with the DOD with contracts containing DFARS 252.204-7012 must have at least a current Basic Assessment against NIST SP 800-171 in order to receive a contract award after November 30, 2020.
- If a company is not subject to DFARS 252.204-7012, then it is subject only to the FAR 52.204-21, Basic Safeguarding of Covered Contractor Information Systems, and is not obligated to submit its score to the DOD through SPRS.
- Although CMMC certification is not imminent for most companies, companies in the defense industry should proactively assess what CMMC certification they may need, and take actions to implement or enhance existing security measures, in consultation with experts and legal counsel.





